Social Engineering Exploits Human Trust and Courtesy to Gain Unauthorized Access
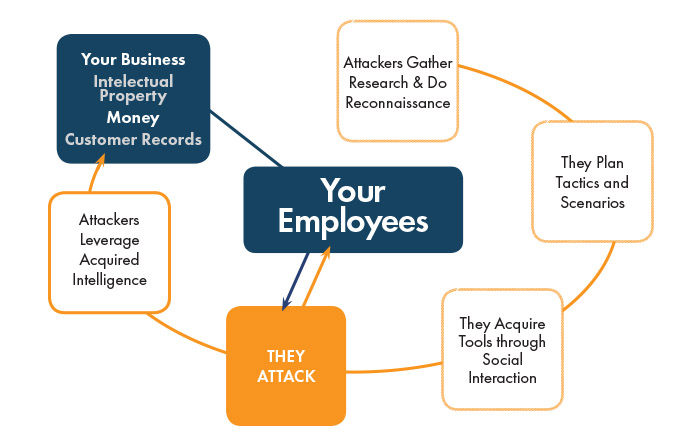
When we talk about security everyone thinks about firewalls and brute force attacks, but most IT administrators have things pretty well locked down on the server side. Some of the recent headline attacks were because of people, not systems. Investigators traced the now famous Hilary Clinton email leak to a hack of John Podesta’s Gmail account, a result of him clicking on a fake Google security alert in a spear-phishing attack. Back-end security will not help when an employee at a work computer clicks a fraudulent link in Facebook, bringing ransomware in the virtual front door. The easiest way into your private information is probably through your employees.
Security Awareness Must be Taught
Social Engineering against human vulnerability is one of the most prevalent attack strategies used today by criminals and other malicious entities. Phishing, fake phone calls, attachments with malware, and even physical access are Social Engineering techniques used to get into your business. Since firewalls and other technical security countermeasures are difficult to bypass, criminals have moved their attacks to the easier, more vulnerable targets: Humans.
Common Social Engineering Attacks
Phishing scams seek to obtain personal or company information with embed links that redirect to fraudulent websites, which appear legitimate. They often use threats, fear, and a sense of urgency to encourage prompt action before thorough consideration. Many Phishing attempts are crude and obvious to spot, which lowers alertness to more sophisticated and refined attacks. Spear Phishing uses similar techniques but the attacks are targeted to a specific individual, often with one or two personal details from the recipient that add to the scam’s legitimacy and likelihood for success.
Pretexting: Attackers focus on creating a pretext, or a fabricated scenario, that they can use to try to steal their victims’ personal information. These attacks commonly take the form of a scammer who pretends that they need certain bits of information from their target in order to confirm identity. Pretexting attacks rely on building a sense of trust with the victim. This requires the attacker to build a credible story that leaves little room for doubt on the part of their target. Pretexting attacks will rely on entry and mid-level employees’ desire to appear courteous and helpful to gain information in small pieces.
Baiting / Quid Pro Quo offers the promise of information, goods, or service as a reward to entice victims. Baiters may offer users free downloads, links to prurient content, gifts, or deals just for logging in. The scams usually have the goal of capturing login information. One famous baiting swindle left USB sticks in a company parking lot. Curious employees picked up the USBs and plugged them into their computers, activating a key logger that captured login credentials. Quid pro quo attacks promise a benefit, usually in the form of a service, in exchange for information. For example, a quid pro quo attack will call random numbers inside a business posing as tech support. If they happen to find someone expecting or even desiring support they will develop a relationship to gain remote access or passwords.
Tailgating: Not all Social Engineering attacks happen on computers. Tailgating or “piggybacking.” is used to gain access to an otherwise secure facility. Tailgaters follow an employee into a restricted area by exploiting employee courtesy. An attacker, in a delivery driver costume, will arrive at the door with an arm full of packages and ask someone entering a secure portal to hold the door. In one case, a security consultant tailgated access to several floors, a data room, and eventually established a base in a third floor meeting room, out of which he worked for several days.
Water Holing: Like animals at a familiar watering hole, people let their guard down on sites they regularly visit. Water holing can be as simple as hiding a fraudulent link in a Facebook post, or on other social media sites, or any well-trusted, popular website. It can get much more complicated as well, exploiting any web location outside a company where that company’s employees regularly interact.
Frontier Computer Corp. is the world’s largest distributor of Peplink connectivity solutions, as well as a provider enterprise IT equipment.